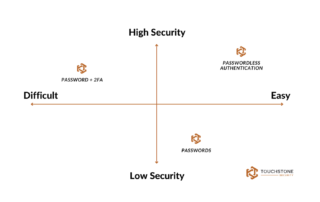
Email Phishing Prevention
Hackers never stop their search for new and more sophisticated ways to breach enterprise security measures. Big data presents a target that tempts criminals, who know they can make a lucrative profit off stolen employee credentials and customer information. Security measures improve more every year to combat cybercriminals, whose technology grows more advanced all of the time. But no matter how ...